Pretexting: Fact or Fiction?
Among the wide range of hacking techniques known collectively as social engineering, pretexting is a tactic that hinges on telling a compelling (and, spoiler alert, fake!) story.
With pretexting, hackers attempt to deceive their targets by establishing a false sense of trust. The hacker uses a fabricated story, or pretext, to get you to download malware, send money or share sensitive information, to name a few examples. As you can imagine, this is a very risky game with serious ramifications if the hacker is successful.
To help you stay safe from a possible pretexting attack, let’s take a look at some of the different ways you might be targeted—and how you can thwart an attempt to coax you into believing a bogus story.
Know the Signs
Here are a few of the most common types of cyberattacks involving pretexting:
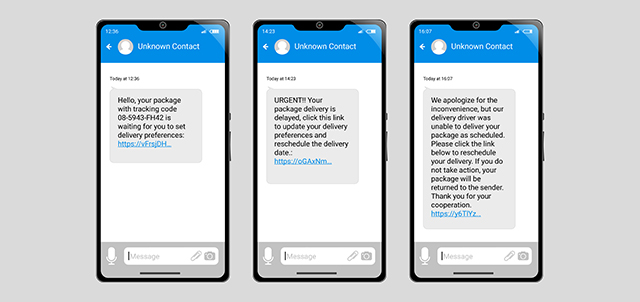
- Vishing and Smishing – These types of attacks use phone calls, voicemails and text messages to trick targets into disclosing or confirming sensitive information. A possible pretexting scenario using these methods could involve an attacker impersonating an IRS agent who tries to scare you into sending money for a past due tax filing, or a UPS worker telling you a package couldn’t be delivered without your address.
- Impersonation – An impersonator imitates the behavior of another actor, usually a trusted person such as a colleague or friend. Hacking into WhatsApp accounts has become a popular way to do this among impersonators. Once the threat actor has access over the hacked WhatsApp or other social media account, they impersonate the target and request money from their contacts, often under the guise of a false emergency with promises of repayment.
- Scareware – This tactic is used to scare people into visiting infected or spoofed (fake, in other words) websites or download malware (malicious software). While surfing the web, you might encounter a legitimate-looking pop-up advising you that your computer is running slow and instructing you to click a link to address the issue—thereby infecting your computer with malware.
Be Proactive About Protection
Taking the following steps can help you stay vigilant and protect yourself against pretexting attacks:
- Verification – If you receive a suspicious inquiry, independently verify the identity of the inquirer before you provide them any sensitive information. Verify their identity by sending an email, reaching out to the institution they say they’re calling from or checking their social media profile.
- Multi-Factor Authentication (MFA) – Use multi-factor authentication (MFA) wherever possible. Even if an attacker obtains login credentials through pretexting, you’re protected by this additional layer of security.
- Be a Skeptic – Be skeptical of unsolicited requests for information, even if they seem to come from a known source, especially when dealing with financial information.
- Stay Informed – Read magazines or news articles about the latest attacks, and be aware of emerging security threats and how the attacks are being carried out.
So, next time you receive a suspicious call, text message or voicemail, stop, think and independently verify the authenticity of the request. The IRS, U.S. Postal Service, UPS, credit card companies and banks will never call you to verify your Social Security number or other sensitive information. When you call them, they may require verifications, but they’ll likely only need the last four digits of your Social Security number. Don’t respond or provide information immediately. By taking these precautions, you’ll significantly reduce the likelihood of becoming a pretexting attacker’s next victim.
Learn more about how to protect your money. If you're the victim of a cybercrime, report it to the FBI’s Internet Crime Complaint Center.